Enhanced Client Proxy Profile Using PAOS Binding
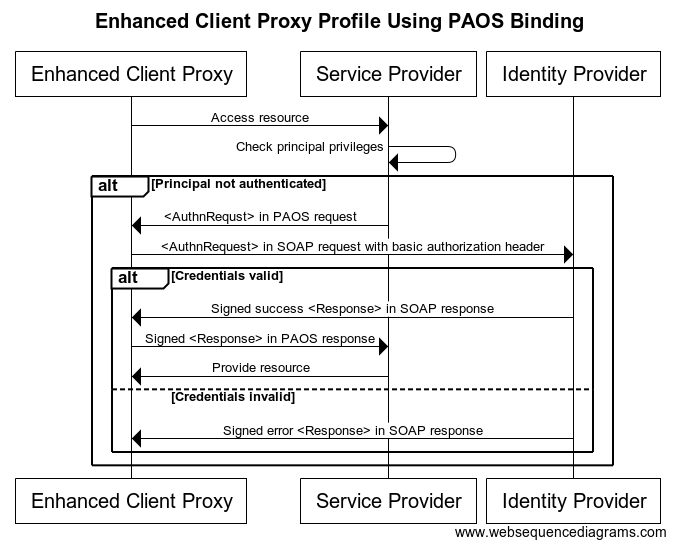
Onegini IDP supports Enhanced Client Proxy Profile Using PAOS Binding. Following graph presents the example flow (for more information please read the documentation).
SAML ECP implamentation in Onegini IDP has some limitations. Currently we do not support
Channel BindingsandHolder of Key.
Authentication
Onegini IDP supports only authentication via basic authorization header so ECP client should attach principal credentials in request header, eg.
Authorization: Basic bG9naW46cGFzc3dvcmQ=
Onegini IDP SAML response on successful authentication
After successful authentication Onegini IDP returns saml:Response with Success status code, eg.
<?xml version="1.0" encoding="UTF-8"?>
<soap11:Envelope xmlns:soap11="http://schemas.xmlsoap.org/soap/envelope/">
<soap11:Header>
<ecp:Response
xmlns:ecp="urn:oasis:names:tc:SAML:2.0:profiles:SSO:ecp"
AssertionConsumerServiceURL="http://service-provider/saml/SSO"
soap11:actor="http://schemas.xmlsoap.org/soap/actor/next"
soap11:mustUnderstand="1" />
</soap11:Header>
<soap11:Body>
<saml2p:Response>...</saml2p:Response>
</soap11:Body>
</soap11:Envelope>
Onegini IDP SAML response on failed authentication
After failed authentication Onegini IDP returns saml:Response with Error status code, eg.
<?xml version="1.0" encoding="UTF-8"?>
<soap11:Envelope xmlns:soap11="http://schemas.xmlsoap.org/soap/envelope/">
<soap11:Header>
<ecp:Response
xmlns:ecp="urn:oasis:names:tc:SAML:2.0:profiles:SSO:ecp"
AssertionConsumerServiceURL="http://service-provider/saml/SSO"
soap11:actor="http://schemas.xmlsoap.org/soap/actor/next"
soap11:mustUnderstand="1" />
</soap11:Header>
<soap11:Body>
<saml2p:Response ...>
<saml2p:Status>
<saml2p:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Responder">
<saml2p:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:AuthnFailed" />
</saml2p:StatusCode>
</saml2p:Status>
</saml2p:Response>
</soap11:Body>
</soap11:Envelope>