Fingerprint authenticator
The Fingerprint authenticator allows users to perform biometric authentication by the use of TouchID. The TouchID functionality is entirely handled by Apple's internal APIs and dedicated hardware - the TouchID scanner and Secure Enclave are encapsulated within the A7 chip which assures that the mathematical representation of a scanned fingerprint is not intercepted, eavesdropped or tampered with. The biggest gain of enabling Fingerprint Authentication is the improved end-user experience. Users are now enabled to access their sensitive data or authenticate transactions using TouchID fingerprint validation. The advantages are that they don't need to remember anything and it's faster.
- Availability
- Fingerprint authenticator registration
- Authenticate using fingerprint
- Fingerprint authenticator deregistration
- Jailbreak detection
Availability
A User can enable fingerprint authentication only if all the following requirements are met:
- The device has hardware support for TouchID
- The device is not Jailbroken
- The user has already registered at least one fingerprint
- The application configuration on the Token Server allows the use of fingerprint authentication
Fingerprint authenticator registration
Registering the fingerprint authenticator requires the user to perform PIN authentication. In order to successfully perform authentication
implementing the userClient:didReceivePinChallenge:forUser: method of the ONGAuthenticatorRegistrationDelegate protocol is required on the delegate.
Implementing authenticator registration is described in the Authenticator topic guide.
Authenticate using fingerprint
Whenever fingerprint authenticator is available and set as preferred the user will be prompted to authenticate with FIDO authenticator instead of
PIN. SDK will call userClient:didReceiveFingerprintChallenge: method on your ONGAuthenticationDelegate. You will be able to choose how to respond to the challenge.
- (void)userClient:(ONGUserClient *)userClient didReceiveFingerprintChallenge:(ONGFingerprintChallenge *)challenge
{
// Continue authentication using fingerprint with default prompt
[challenge.sender respondWithDefaultPromptForChallenge:challenge];
// Or use custom prompt
[challenge.sender respondWithPrompt:@"Confirm money transfer" challenge:challenge];
// Fallback to pin if needed
[challenge.sender respondWithPinFallbackForChallenge:challenge];
// Or cancel challenge
[challenge.sender cancelChallenge:challenge];
}
Because fingerprint scanning is not perfect (e.g. the user may have wet or dirty hands also the temperature may affect the scan result) the user can always choose to fallback to PIN authentication by pressing the "Cancel" button:
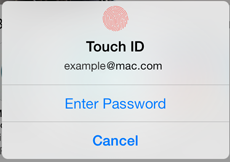
Also, after failing to scan a fingerprint for the allowed number of times, the SDK will automatically fallback on the PIN authentication method. If the user will not be able to provide a valid PIN within the allowed number of times, he will be deregistered.
Fingerprint authenticator deregistration
Implementing authenticator deregistration is described in the Authenticator topic guide.
Jailbreak detection
The Jailbreak detection check is applied even if Jailbreak detection is disabled for the application. The reason is that Jailbroken devices are more vulnerable, as the application sandbox as well as KeyChain can be violated. The situation is even more serious for clients who are not using tampering protection and/or are running on older versions of iOS.