Resource gateway configuration
In the overall architecture it is the responsibility of the resource gateway to grant or block access to specific APIs or resources. To evaluate if a client is allowed to use a resource the resource gateway must validate an access token. The Token Server provides an API so access tokens can be validated. Access to this API is restricted for OAuth clients with a specific role. Hence, the resource gateway acts as an OAuth (web) client and needs to be configured as one.
Configuration a resource gateway as web client
The resource gateway can be configured as an OAuth web client via the admin console. In order to create a resource gateway, go to the Configuration section in the
admin console and open the Web Clients tab. Here you can find all the existing web clients. To add a new one, click on the Add button. The following
form will appear:
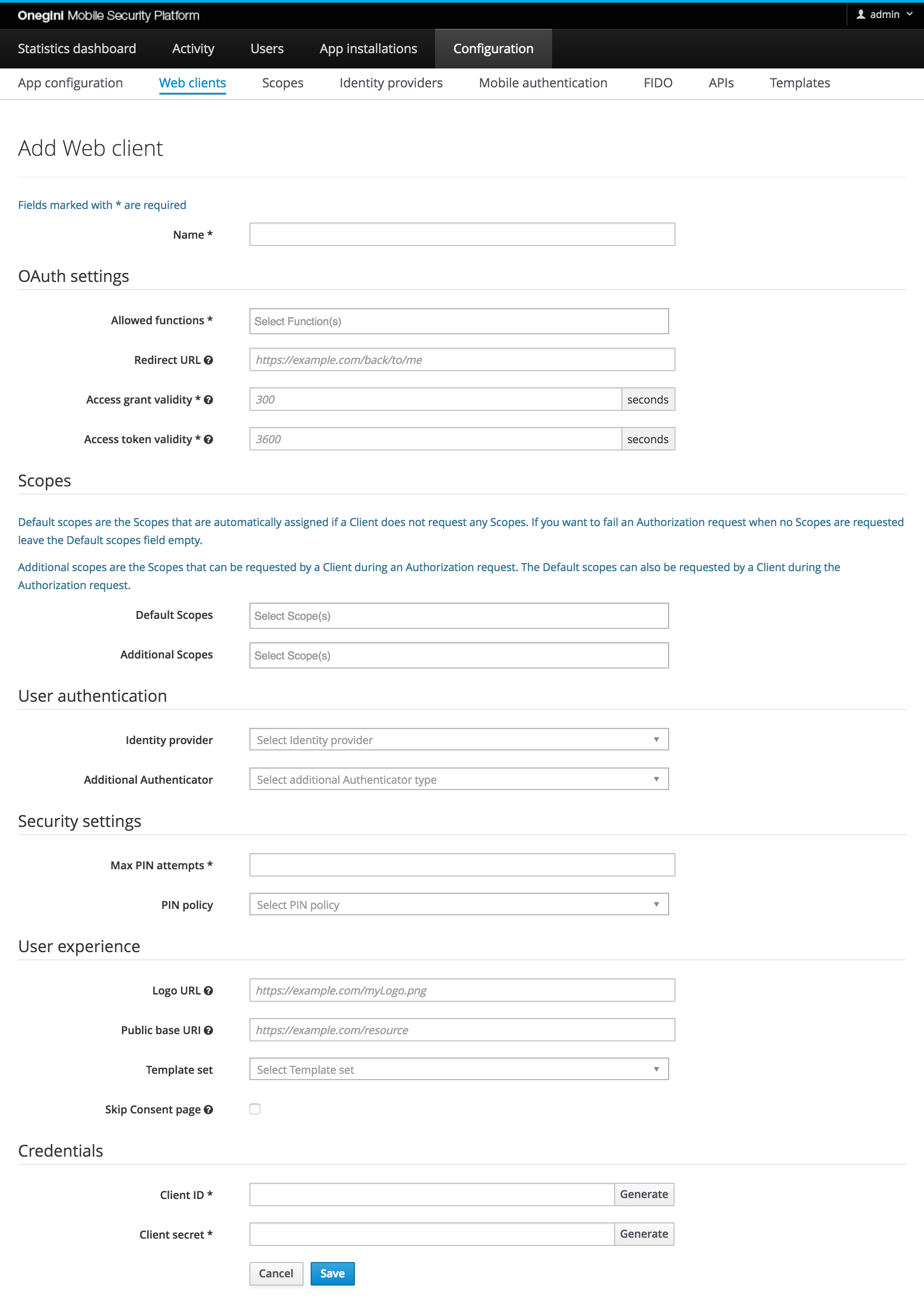
A resource gateway differs from a normal web client, it only requires a few fields to be filled in the form:
- Name - The resource gateway is referenced using the value form this field.
- Allowed functions - The resource gateway uses only one function:
VALIDATE_ACCESS_TOKEN, and that one must be selected in this field. - Client ID, Client secret - This pair of values is used to authenticate the resource gateway when it communicates with the Token Server. Those values can be filled or generated. This information is sensitive and should be treated accordingly.
- Public base URI - the base uri (public endpoint) of the resource gateway.
The other fields should stay empty or the default values should be set. Access Grant Validity, Access Token Validity and Max PIN attempts are currently required to fill in. Enter the value 1 to submit the form.
Configure communication with the Token Server
The resource gateway communicates with the Token Server to validate access tokens
provided by OAuth clients. In order to do that, a resource gateway uses the /oauth/token endpoint of the Token Server.
To allow communication to this endpoint, the network configuration should be adjusted. Especially network traffic from the resource gateway to the Token Server
must not be blocked by firewalls). The same /oauth/token endpoint might already be publicly available since this endpoint is also used by mobile applications
to retrieve access tokens.