SAML Service Provider Configuration
The Token Server can act as a SAML Service Provider during the authentication of a user, for this reason the Token Server exposes metadata. The SAML metadata exposed by the Token Server can be found via the url oauth/saml/metadata. This section describes how to adapt the values used in the metadata for this Service Provider.
In order to configure SAML Service provider usage, go to the Configuration section of the administration console, then System and choose the SAML Service provider tab.
- Configure Metadata of the SAML Service Provider
- Configure SAML Service Provider key store encryption key
- Configure SAML requests signing
- Configure location of the SAML velocity log file
- Confgure SLO (Single logout) feature
The picture below shows the SAML Service provider view in the Admin Console with an example configuration.
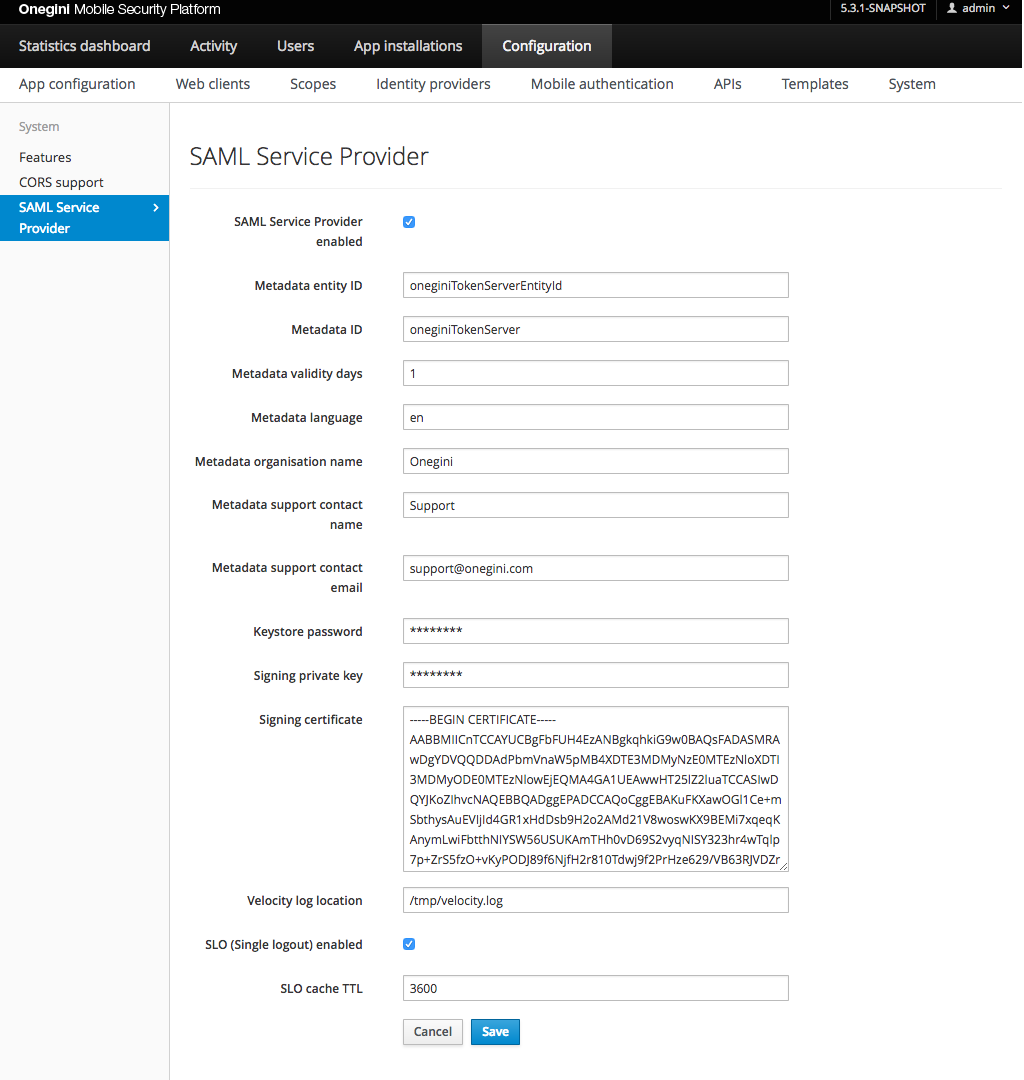
Configure Metadata of the SAML Service Provider
In order to configure Metadata for the SAML Service Provider configure the following fields:
| Field name | Default value | Description |
|---|---|---|
| SAML Service Provider enabled | true | Indicates if SAML endpoints on the Token Server are enabled. Without enabling these endpoints the samlUserAuthenticator can not be used. |
| Metadata entity ID | oneginiTokenServerEntityId | Entity identifier of the SAML Service Provider. |
| Metadata ID | oneginiTokenServer | Identifier of the SAML Service Provider. |
| Metadata validity days | 1 | Indicates the validity of the SAML metadata of the Service Provider in days. |
| Metadata language | en | Language code used in the descriptions etc in the SAML Service Provider metadata. |
| Metadata organisation name | Onegini | Name of the organisation used in the SAML Service Provider metadata. |
| Metadata support contact name | Support | Name of the support contact person used in the SAML Service Provider metadata. |
| Metadata support contact email | [email protected] | Email address of the support contact person used in the SAML Service Provider metadata. |
Configure SAML Service Provider key store encryption key
In order to configure key store encryption key for the SAML Service Provider set the following field:
| Field name | Default value | Description |
|---|---|---|
| Keystore password | --- autogenerated --- | Password used to encrypt the SAML Service Provider key store. |
Configure SAML requests signing
In order to configure SAML requests signing set the following fields:
| Field name | Default value | Description |
|---|---|---|
| Signing private key | --- autogenerated --- | The private key used by the SAML Service Provider to sign requests. |
| Signing certificate | --- autogenerated --- | The public key / certificate of the SAML Service Provider which can be used by the IDP to validate the signature. |
Configure location of the SAML velocity log file
In order to configure location of the SAML velocity log file set the following field:
| Field name | Default value | Description |
|---|---|---|
| Velocity log location | /tmp/velocity.log | Location on the file system where the velocity log file generated by the SAML module will be stored. |
Note: Applying this value change requires Token Server Engine Application to be restarted.
Confgure SLO (Single logout) feature
The goal of the SLO feature is to logout user from a web client when their SAML session is terminated by the SAML Identity Provider. In order to configure using SLO configure the following fields:
Note: Applying SLO cache TTL value change requires Token Server Engine Application to be restarted.